In my previous post, I explained how I use the analogy of securing your organization’s data as similar to protecting the valuables in your home to help demystify cyber security. I like to use these types of analogies when discussing cyber security with organization leaders to give them straightforward examples of actions they can take to protect their data.
This is particularly effective when speaking with non-technical senior-level executives. It’s unreasonable to assume that these individuals have a comprehensive grasp of cyber security and how they should be leading their organization’s activities. It is equally unreasonable to assume that the individual leading the information technology (IT) function is fully versed in information security. Even if they are knowledgeable, a lot of data protection-related activities fall outside of their scope of responsibility.
The intent of these types of analogies is not to insult someone’s intelligence but rather to cut through the overwhelming amount of terminology and technology to communicate tangible, relevant concepts that can help them protect their organization’s data.
As I mentioned previously, an easy way for people to think of securing their organization’s data is to think about the actions they take at home. Would you leave valuables laying out in the open? Would you leave your windows and doors wide open when you aren’t home? Would you advertise to criminals that you don’t secure your valuables? Would you not insure your valuables in the event of theft? Take a second and reflect on the things that you do at home to secure your belongings. No one would consciously leave their residence unprotected. The same thing needs to hold true for their businesses/organizations.
Organizations that have well-thought-out plans will be safer and protect their data more consistently. Protection measures go far beyond technology-related measures and include policies and raising an organization’s information security awareness. These same measures have a very direct correlation to what organizations should be doing to protect their valuables (data). The table below depicts some of the policy- and organization-related measures people take in their homes and the corresponding ones they can use in their organization.
Examples of Policy and Organization Measures
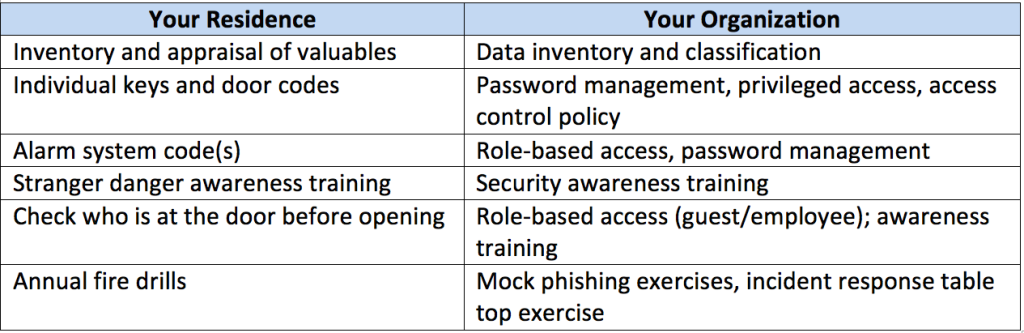
This type of analogy is not only useful in helping executives understand what their organizations can do, but also in helping their entire organization to understand the various components that make up a strong approach to data protection.
COMPASS provides a practical yet comprehensive approach to cyber security. If you would like to learn more about our approach and how your organization can benefit, please contact us.
