Organizations continue to struggle with how to implement their cyber security program. Often, they fail to realize that their approach should be based on the principles of enterprise risk management. Company-wide security incidents and data-breach risks should be treated as seriously as an internal natural disaster. Cyber security is a risk so complex that it touches every aspect of an organization, and the basic principles for addressing such risks are very similar.
Enterprise risk management is actively identifying, assessing and addressing risks that have the potential to negatively impact the entire organization. Because there are a number of ways data breaches can occur (e.g., an employee accidentally leaving an unencrypted, company-owned mobile device in a public place like a cab or hotel), organizations must understand and address each scenario individually.
Examples of potential risk-mitigation strategies for cyber security-related scenarios follow.
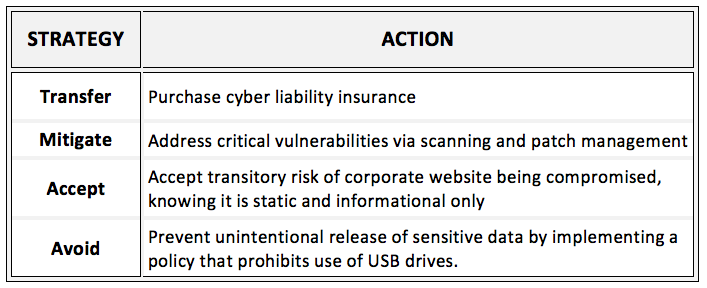
Those organizations with existing risk-management processes should ensure cyber security-related risks are included as part of their standard activities. Cyber-related risks must be identified, analyzed and prioritized like any other risk an organization might face. Without a clear understanding of unique risks and vulnerabilities, organizations will be challenged. Thus, they must assess their risks across the three pillars of cyber security—people, policy, and technology—to gain insight and develop appropriate remediation plans.
Following is a sequence of high-level steps organizations should follow as part of their cyber security risk-management process:
- Assess your organization across all 3 pillars (people, policy and technology)
- Develop a prioritized remediation action plan
- Implement the remediation action plan
- Develop a long-term cyber security program roadmap based upon assessment findings
- Implement and maintain cyber security roadmap
- Regularly assess the organization’s cyber security hygiene
Organizations must not allow the complexity and scope of cyber security prevent them from implementing an enterprise risk-management-based approach. COMPASS provides a practical yet comprehensive approach to cyber security. To learn more about our approach and how we can help protect your organization, please contact us.
