I am constantly amazed at how little organizations are doing to protect their data, regardless of their industry or size. I don’t mean spending a lot of money on the latest and greatest technology. I mean taking basic steps like training their employees on security awareness or optimizing the technology that they already own.
Why have these organizations done so little? Their leaders often tell us that they:
- Don’t think they are a likely target of bad actors, or that if they do have a data breach it won’t impact them that much;
- Are overwhelmed with the entire concept of cyber security and don’t know where to begin;
- Think that protecting their data is the information technology department’s sole responsibility.
These excuses reflect the common view of cyber security as a complex and overwhelming topic, which often leads to inaction. So many leaders are essentially paralyzed by not having a structured path forward.
In response, I often encourage people to think about the actions they take at home. In truth, most of the leaders I talk to are likely to do more to secure their homes than they are to secure their organizations. Yet the principles are surprising similar.
I ask them: Would you leave valuables lying out in the open? Would you leave your windows and doors wide open if you aren’t home? Would you advertise to criminals that you don’t secure your valuables? Would you not insure your valuables in the event of theft? Would you not take extra precautions if there were a string of thefts in your neighborhood?
No one would consciously leave their home unprotected. The same thing should hold true for protecting your organization’s data. Organizations that have well-thought-out plans will be safer and protect their data more effectively and consistently.
One pillar of good cyber security is technology. The table below depicts some of the technology related measures people take in their homes and the corresponding measure that relates to their organization. In my next blog post, I will focus on the other two pillars, the people and policy aspects of data protection, and the correlation between your residence and your organization.
Examples of Security Measures
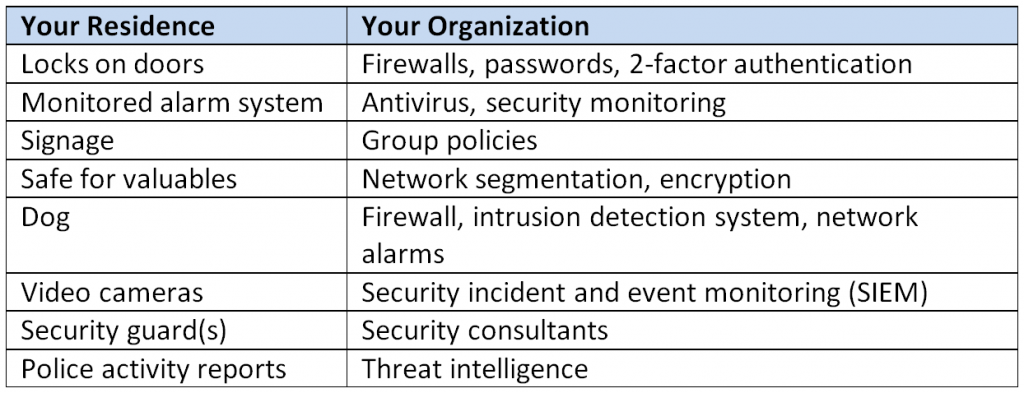
Protection measures you might take in your residence include locks on doors, outside floodlights, a dog, a safe, an alarm system, video cameras, a certain room where you keep most of your valuables. These same measures have a direct correlation to what organizations should be doing to protect their valuable data.
If your organization uses technology, then it is vulnerable to a bad actor(s) trying to steal your sensitive data, which may include Personally Identifiable Information (PII), Protected Health Information (PHI), or confidential and proprietary information. Developing a well-thought-out security roadmap that incorporates a combination of technology-, policy-, and people-related security measures can significantly improve your organization’s data protection posture.
Organizations should take a layered approach, known as defense in depth, to create a series of protection mechanisms. For a deeper conversation about how to get started, feel free to reach out.
